Most Common IoT Architecture : A Comprehensive Guide
The Internet of Things (IoT) is a major force behind innovation across industries such as home automation, health, commercial industry, and farming. IoT architecture is at the center of this development as it also presents the blueprint or infrastructure that defines how the devices, networks, and platforms ought to work. Choosing the right IoT architecture is crucial to attain scalability, security, and management of data. This blog (article) aims to identify the various common architectures of IoT, their components, layers, and their use in different/multiple sectors.
What is IoT Architecture?
IoT architecture can be described as the structure of the IoT ecosystem including the hardware, software, and networking. It allows the acquisition and transfer of information as well as the processing of this information while at the same time providing for the interconnectivity, protection, and control of a massive number of integrated devices.
Importance of Internet of Things Architecture
A well-designed IoT architecture is fundamental for
Efficiency
Enabling smooth data transfer between devices, gateways, and cloud services.
Scalability
Allowing the system to accept other devices without dropping its performance.
Security
Protecting information and gadgets through the use of encryption and protocols.
Real-Time Processing
Suitable for fast decision-making requirements such as industrial automation and intelligent healthcare.
Common IoT Architectures
1. Three-Layer IoT Architecture
One of the earliest and most straightforward IoT architectures is the three-layer model which is composed of the following layers…
Perception Layer
- Purpose: In this physical layer IoT devices, sensors, and actuators collect information from the environment they are in.
- Components: Sensors, RFID tags, actuators.
- Function: Receives data from the lower layer and sends it to the higher layer.
Network Layer
- Purpose: Responsible for passing data collected at the perception layer to other devices, servers, and other data centers for analysis.
- Components: Routers, gateways, communication protocols (Wi-Fi, 4G/5G, Zigbee).
- Function: Provides the guarantee of secure data transmission within the network.
Application Layer
- Purpose: Takes data from the previous layers and provides services for end-users in response.
- Components: Smart home, smart city, connected car, wearables, smart workplace, smart retail, smart agriculture, smart grid, smart industry, smart transportation, smart health, smart home security, connected home, connected cars, connected retail, connected farms, connected factory, connected city, connected building, connected home appliances, connected home security, connected car security, connected retail security, connected farm security, connected factory security, connected city security, connected building security, etc.
- Function: It enables the user to communicate with the IoT system including the uses of smart homes or industry control panels.
Advantages of Three-Layer IoT Architecture
- Simple and easy to implement.
- Recommended for less complex IoT systems, which are smaller in scale.
Disadvantages of Three-Layer IoT Architecture
- Limited scalability
- Some of the fundamental security measures may not be sufficient to support complex operations.
2. Four-Layer IoT Architecture
The four-layer IoT architecture is derived from the three-layer model by incorporating a processing layer making it more appropriate for complex IoT scenarios.
Perception Layer
Similar to the three-layer architecture, it performs the same function which is the collection of data or information from the environment.
Network Layer
More versatile to support the integration of more complex networking opportunities such as edge computing networks.
Processing (Middleware) Layer
- Purpose: Responsible for data pre-processing, data cleaning, and data reduction before forwarding the data to the cloud.
- Components: Smartphones, routers, local servers, fog nodes.
- Function: It performs local computation to minimize latency and bandwidth consumption.
Application Layer
Similar to the three-layer model but with extra capabilities for working with other types of applications, for example, real-time industrial analytics.
Advantages of Four-Layer IoT Architecture
- More appropriate for larger and additional complicated IoT applications.
- Reduces latency by allowing data processing at the edge or fog layer.
Disadvantages of Four-Layer IoT Architecture
- Difficult to implement and maintain than the other models.
- Increased energy consumption because of the need for local processing.
3. Five-Layer IoT Architecture
The five-layer architecture is a more complex model that is intended to fulfill business requirements and address data management in a better way.
Perception Layer
Acquires information through sensors and actuators, as was the case with the previous architectures.
Network Layer
Serves as an interface for device-to-device, device-to-gateway and gateway-to-cloud communication.
Processing Layer
Relies only data aggregation, filtering, and calculation at the edge or fog level while limiting the consumption of additional clouds.
Business Layer
- Role: It controls business logic and decision-making that is informed by the processed data (collected data is transformed into business decisions after processing).
- Components: Business activities, corporate applications (for example, customer relationship management, enterprise resource planning systems).
- Function: Makes sure that IoT systems are properly integrated with business objectives by turning the generated data into business decisions. (it results in good ROI and ultimately the business grows and enhances rapidly)
Security and Management Layer
- Role: It aims at controlling the security of the particular device, protection, identification of users, and their ability to gain access to the information.
- Components: Encryption algorithms, authentication protocols, security frameworks (SSL, TLS).
- Function: In this later it only allows the specific users to open the system and protect/safeguard the equipment from online dangers.
Advantages of Five-Layer IoT Architecture
- Fiver layer IoT is highly scalable and best-suitable for enterprise Internet of Things applications.
It suits real-time data processing and business intelligence
Disadvantages of Five-Layer IoT Architecture
- It is complicated and expensive to deploy.
- Demands very strong base and control mechanism.
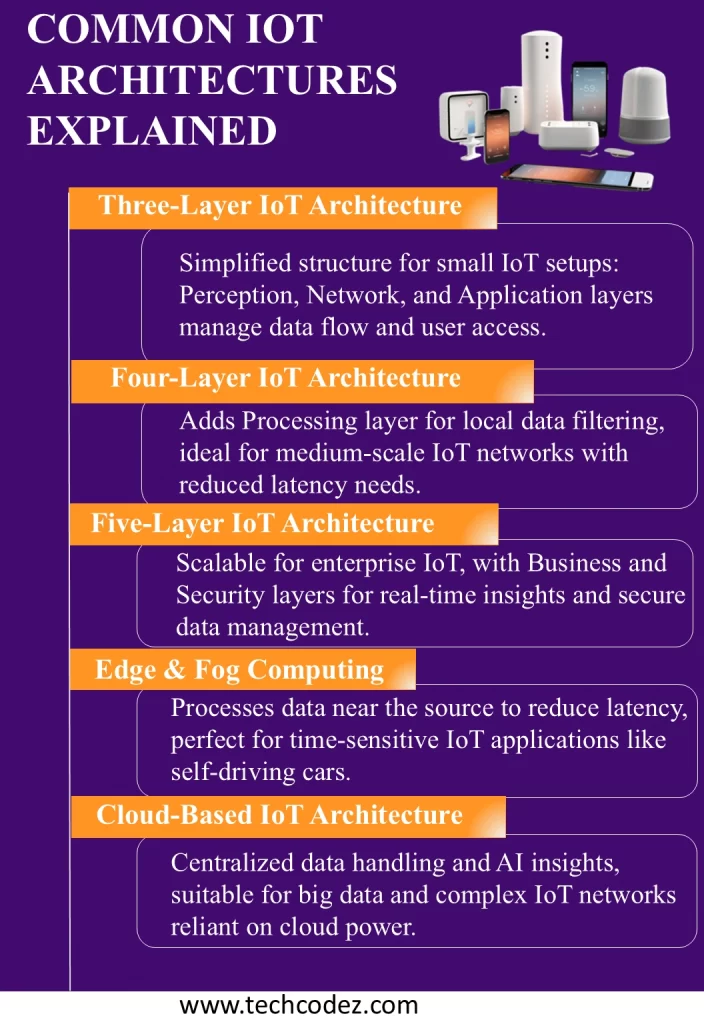
4. The IoT Architecture of Edge and Fog Computing
New concepts in computing architectures have been designed to overcome the constraints associated with cloud-based environments for use in real-time on-the-spot applications.
Edge Computing
- Role: This IoT architecture helps to analyze data on the network periphery, at “the edge” near the source, for example, in IoT devices.
- Its function is to save data that can be processed on the edge to be sent to the cloud, which either can reduce latency or time response for quick decision-making real-time applications such as self-driving cars.
Fog Computing
Grows the concept of edge computing by building a network of nodes that perform computing at the edge.
Solves the dilemma between cloud computing and edge devices, balancing and minimizing the interaction and utilization of resources, and data transfer to the cloud.
Pros of IoT Architecture of Edge and Fog Computing:
- Reduced latency since data was processed closer to the source.
- Less quantity of data to the cloud
- Therefore saving bandwidth and energy.
Disadvantages of the IoT Architecture of Edge and Fog Computing:
The management of a decentralized network is not easy. As data is processed outside centralized cloud environments, security risks become higher.
5. Cloud-Based IoT Architecture
A cloud-based IoT architecture makes use of the cloud for storage, computation and analysis of data. IoT devices transmit their information to the intermediary cloud servers for analysis.
Perception and Network Layers:
It work similarly to those in other architectures but depends on cloud integration.
Cloud Processing Layer
- Role: Provides data acquisition and management, as well as data analysis services in the cloud computing environment.
- Components: AWS IoT, Microsoft Azure IoT Hub, Google Cloud IoT.
- Function: It allows for more in-depth analysis of the data retrieved from IoT devices and also enhances the use of machine learning and artificial intelligence to make decisions.
Application Layer
Enables users to control IoT devices and access IoT information by using applications and services on the cloud from any place.
Advantages of Cloud-Based IoT Architecture
- Have a high capacity for handling large amounts of data for efficiency.
- Suits for usage in big data analysis
- It is not a difficult (herculean) task to restore the data.
- Cloud-based IoT service providers leverage the best technologies to protect data, systems, and workloads.
- Cloud-based IoT services can help to protect and secure data through encryption, authentication, and backup.
- IoT platforms that are based on the cloud and discarded or diminish the initial capital cost on hardware, software and maintenance.
Disadvantages of Cloud-Based IoT Architecture:
- Dependent on a steady connection to the internet.
- Some applications may experience latency problems.
Understanding and selecting the appropriate IoT architecture to support the IoT system in running effectively and successfully is important (a key aspect). Each architecture provides diverse capabilities, and the chosen architecture depends on the system’s needs. With IoT penetration across industries, there is a need for a solid, scalable, and secure architecture that will support the functionality of devices and systems. As simple as the three-layer model or as complex as the five-layer or cloud model, each architecture has its benefits and is appropriate for specific applications. Choosing the right architecture for IoT depends on many factors such as business requirements, the complexity level of the system and how data is to be handled.
Pros of IoT
Execute Multiple Tasks
IoT devices are multitasking in nature as they can collect/gather, process, and send information.
Easiest Internet Connectivity
IoT devices are easy to connect to the internet to realize different forms of communication and data sharing in real time.
Graphical User Interface (GUI)
Most IoT devices, including the Raspberry Pi, switch to an HDMI port to function in GUI mode, thus providing a more intuitive approach to user inputs and outputs.
Server-Based Applications
These connected devices work with server applications and can be controlled through SSH for command-line activities and FTP for file transfers.
Reliability for Software Applications
IoT systems are very suitable for the constant execution of software applications and services especially in automation and monitoring.
Cons of IoT
Security Concerns
IoT devices are easily compromised, and the use of IoT technology exposes a user’s data, as well as the overall system, to hacking and cyberattacks.
Privacy Issues
The nature and the constant accumulation of personal data by IoT devices raise questions regarding its usage and distribution.
Dependence on Technology
The use of IoT devices makes a system more prone to system failures that would eventually lead to service disruptions.
Complexity
The use of multiple IoT devices complicates the network and imposes additional requirements on its maintenance and technical support.
High Initial Costs
The establishment of an IoT ecosystem requires a relatively large amount of money to be invested in devices, networks and software.
Battery Life Limitations:
Some of the IoT devices are constrained by low battery power which is a hindrance to its longevity.
Job Displacement
Use of IoT systems in automating tasks leads to unemployment because those tasks that were done manually are eliminated.
Regulatory Gaps
This makes IoT vulnerable to legal risks and data handling and security problems because there are no comprehensive laws regulating IoT.
Some Modern Applications of IoT
Smart Grids and Energy Saving
IoT allows for the remote control and measurement of energy consumption to control energy usage in smart grids.
Smart Cities
IoT drives the management of infrastructure that includes street lighting, traffic signals, and waste collection enhancing urban functionality
Find More About Smart Cites
Smart Homes
Smart home technology is an application of IoT that controls lighting, appliances, security and many other aspects of a home to make them convenient and safe.
Healthcare
The use of IoT in healthcare involves wearables, remote monitoring, and real-time tracking of health, changing the face of medical services.
Earthquake and Climate Detection
Wireless IoT sensors detect seismic activities to give an early signal on the effects of the calamities.
Hazard Detection
The IoT is applied to radiation and hazardous gas detection that enables monitoring of the level of radiation and gas leakage in real-time and alerts the necessary concerned authorities or parties in industrial areas.
Smartphone Detection
Smartphones are identified and monitored using IoT in retail, security, and traffic management.
Water Flow Monitoring
Concerning resource management, IoT devices assist in monitoring water detection and leakage to solve the problem.
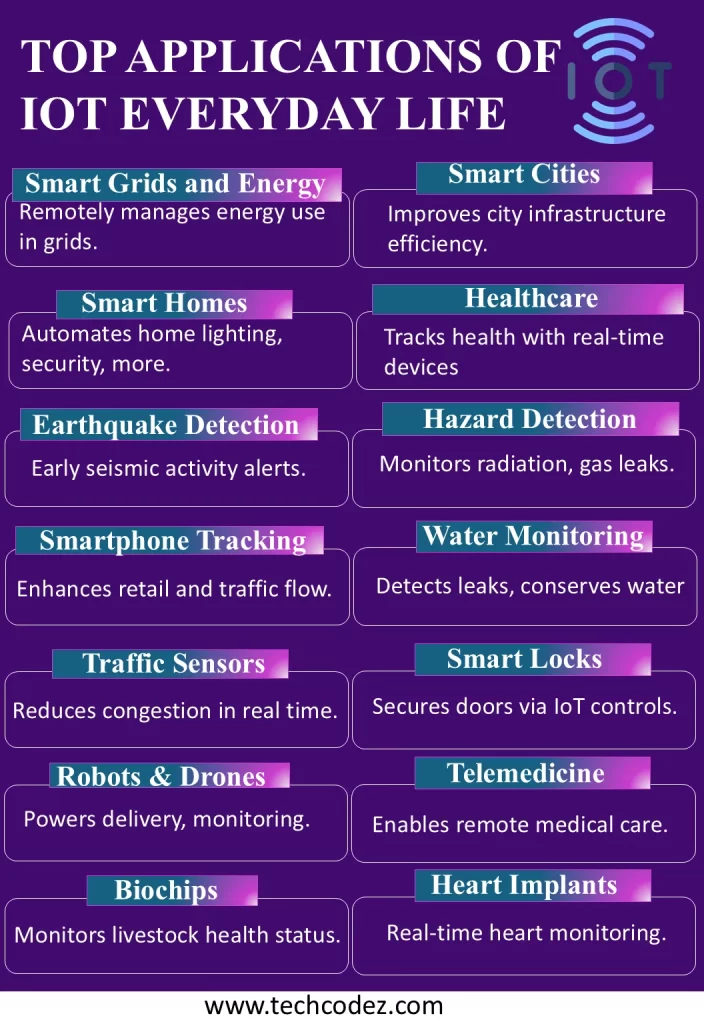
Traffic Monitoring
The application of IoT sensors for traffic data collection in real-time enhances traffic flow and also reduces crowding or jamming.
Smart Door Locks
Intelligent security systems ensure that home security is improved by enabling door security through IoT.
Robots and Drones
These devices use IoT to accomplish assignments such as delivery of parcels, monitoring and manufacturing.
Telemedicine
Telemedicine platforms mean that IoT makes it possible for people to be diagnosed and treated from the comfort of their homes.
Biochip Transponders
In livestock farming, IoT-based biochips are used in monitoring the health status of animals.
Heart Monitoring Implants
Smart objects including pacemakers are constantly monitoring heart rhythm and transmitting data in real time to physicians.
Sensors Employed in the Sensing Layers of the Internet of Things
- Temperature Sensors: Control environmental or system temperature.
- Humidity Sensors: Determine the humidity.
- Light Sensors: Determine the amount of brightness in a particular setting.
- Motion Detectors: Monitor activity in zones such as security or even the lighting system.
- Pressure Sensors: Determine force or pressure in a system.
- Gas Sensors: To sense gases such as carbon dioxide or any toxic material present in the air.
FAQs
What is IoT Architecture?
IoT architecture means a set of components that are hardware, software and networking in an IoT environment. This architecture enables the collecting, forwarding, and processing of data, device connection, security, and control.
What are the Three-Layer IoT Architecture?
The three layers of IoT architecture are as follows:
Perception Layer: Definite for collecting data.
Network Layer: Sends data to server or data center for processing.
Application Layer: It delivers services to the end-users agreeing with the result obtained from the analysis.
What are the differences between Four-Layer IoT Architecture and Three-Layer Architecture?
The Four-Layer IoT Architecture added a new layer, known as the Processing Layer or Middleware, which executes activities that include filtering the data received from the Access Layer, aggregating processed data, and local processing of specific data. This cuts down on latency and bandwidth very considerably, especially by providing realism for edge or fog computing.
What are the benefits of Edge and Fog Computing in the IoT Architecture?
There are several benefits associated with edge and fog computing: closer processing, less bandwidth usage and lower latency, all of which are paramount for real-time applications which include self-driving cars and manufactory automation.
What are the drawbacks of adopting Cloud-Based IoT Architecture?
Some of the main drawbacks of cloud-based IoT architecture include the following; this model relies on an internet connection, there may be delays in some processes that require quick response, and there is a possibility that the system may be hacked because most of the operations are centralized.
Find More About IOT