Virtual Desktop Security Best Practices for Financial Institutions
Financial institutions deal with very sensitive information therefore they need proper data security. At the same time, this industry is rather saturated, and that is why it is crucial to achieve maximum efficiency. This balance can only be achieved through strategic technologies, including Virtual Desktop Infrastructure (VDI).
Virtual Desktop Security Best Practices examine the relevance of VDI in the financial industry and the right approach to adopting it in financial organizations, focusing on how it can improve security and efficiency.
Moving to Virtual Desktop Infrastructure in the Financial Sector
VDI stands for Virtual Desktop Infrastructure, which is a technology that allows for the merging and virtualization of the desktop environment and the results provide secure access to the work environment on a variety of devices from any location or remote place.
Benefits of Virtual Desktop in the Financial Sector
When applied to the financial sector business, VDI plays a priceless role in securing data from unauthorized access and simultaneously increasing its performance. The following points highlight the pivotal benefits of VDI in financial organizations:
Data Security:
Banks deal with large amounts of data/information that is often confidential, this includes client details, account details, transaction records, and analytical work among others. All data is stored on secure servers, and VDI reduces risks that are inherent to data leakage and unauthorized access.
Regulatory Compliance:
These financial industries work on following GDPR, HIPAA, PCI, as well as other requirements. These compliance requirements can be met through VDI by ensuring safe storage of data, as well as making it possible to keep detailed audit trails.
Remote Accessibility:
With the globalization of the economy, financial workers need to ensure that they can access their workplaces securely from home. VDI helps this by allowing employees to work remotely and from home or while on a business trip.
Disaster Recovery:
A disaster recovery plan is also crucial for financial associations. VDI makes backup and restoration extremely easy thus allowing important data and applications to be restored in cases of disruptions.
Enhanced Collaboration:
Effective collaboration of VDI in finance provides secure access to shared applications and documents, streamlining teamwork and enabling informed decision-making.
Cost Efficiency:
It helps to minimize the reliance on actual desktops and makes the work of IT departments easier. In addition, it sustains existing hardware for more extended periods, making technology consumption less unsustainable.
Security Benefits of VDI
It is known for providing a secure and effective means of addressing the needs of remote employees while going beyond the concept of BYOD. Key security benefits include:
- Centralized Data Security: virtual desktops guarantee that all the sensitive data is stored on the organizational servers regardless of the location of the user. This centralization significantly reduces the risk of data breaches and helps with compliance with the regulation by avoiding data leaks.
- IT Oversight and Control: While other forms of BYOD are not well managed, it allows IT departments to retain control of security measures. IT groups can control the timing, carry out security scanning, and guarantee that networks are safe from cyber criminals.
- Data Centralization and Protection: VDI reduces the risk of data leakage by storing desktops and data in data centers, instead of on endpoints. Data is safe in the event that the device is lost or stolen because data is not stored locally. This kind of approach also enhances the generic backup and recovery processes and hence increases organizational efficiency.
- Secure Remote Access: VDI helps companies to effectively implement remote computing; with built-in encryption, multiple factors authentication and access rights systems. These measures help to protect data during its transmission and support business processes in case of, for example, remote work or disaster.
- Consistent Security Policies: Security updates, patches and configurations can easily be implemented by administrators on all the virtual desktops without compromise via VDI. This reduces the risk stemming from outdated software, misconfigurations, and the like, the result is a healthy, aligned, and consistent security stance.
Security Risks and Threats to Virtual Desktops
This is considered to be a secure solution for remote work, but it has its weaknesses as well. Potential security risks associated with VDI include:
Hypervisor Vulnerabilities
A VDI environment is built on the use of hypervisors to host multiple virtual desktops on a single host. A security failure on the hypervisor compromises the isolation mechanisms, allowing it to be accessed by a third party.
Network Weaknesses
Despite the improvement of endpoint security when implementing VDI for remote employees, the virtual desktops are still linked to the company’s applications and networks. Lack of administration and proper security measures give opportunities to string attackers around network problems. They can gain access through infected virtual desks, and penetrate deeper into the organization’s network.
Human Factors
Employee behavior or activities is also a major subject/issue in security. Employers require proper monitoring/regulation/rules and security to reduce the risks linked to potential human mistakes or intentional misconduct in the context of VDI environments. Technical fundamental training is crucial for all employees especially for newbies to avoid any mistakes.
Unpatched Virtual Machines
Like physical computers, virtual machines need updates to patch up vulnerabilities in their software. Skipping, delaying or avoiding vulnerability scans or not applying patches when released, a system is susceptible to attack.
Data Exposure
Centralized desktops and data in a VDI environment pose several risks if the wrong hands get in or if there is a breach in security. Reasonable technical protection measures are required to ensure the confidentiality of the data. Insufficient or poor user authentication will also leads to breaches of security. MFA is necessary to mitigate the threats resulting from the breach of user accounts.
Endpoint Security and Software Vulnerabilities
The devices that are used to access VDI environments must be protected. Open accesses on endpoints will be a vector for malware or malicious ventures. The components of VDI that are not updated involve the system to certain susceptibilities for hypervisors and other components. It is essential to keep receiving updates and patch them on time.
When an organizations manage to effectively address these risks through profound measures like encryption and compilation of rigid access controls as well as constant updates, then it will be possible to come up with a safer virtual desktop environment.
Virtual Desktop Security Best Practices
How to alleviate threats and risks connected with virtual desktops?
To mitigate the inherent risks associated with VDI solutions, financial institutes must have to adopt a wide but protective range of best security practices.
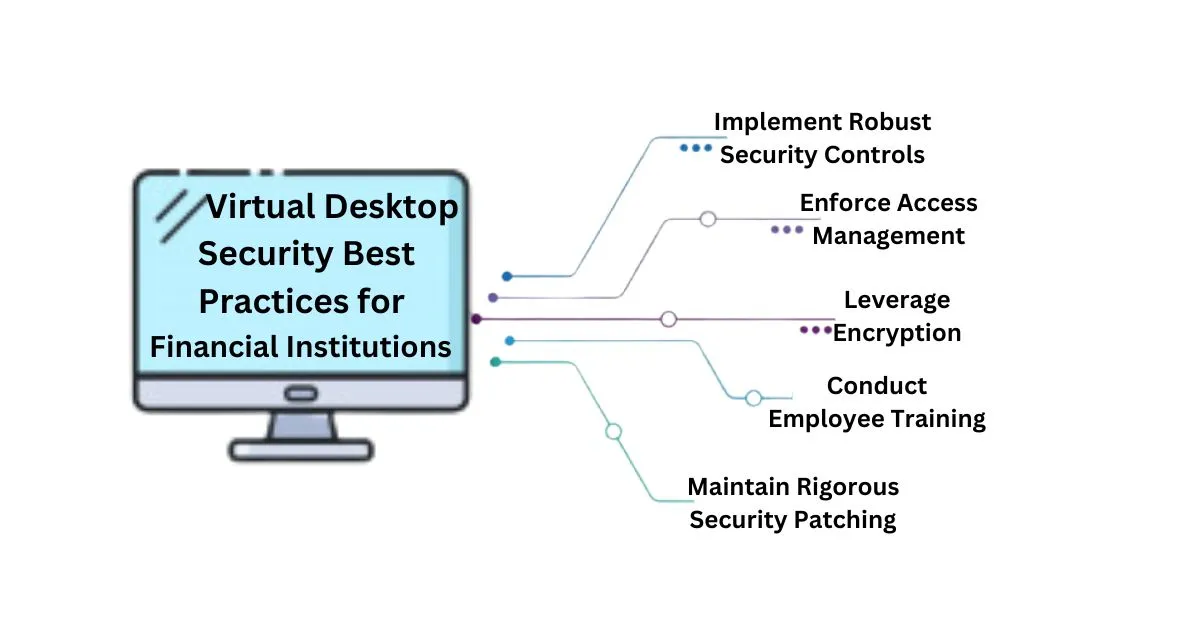
- Implement Robust Security Controls: Security policies are necessary to control the ways that employees use virtual desktop workstations to reduce threats and meet the requirements of regulations/rules.
- Enforce Access Management: In line with the least privilege concept, the access management policies should only allow users access to privileges that are relevant to their positions. This reduces the risk that may stem from a security breach among the IT facilities of the institute.
- Leverage Encryption: Data that exists in or is processed should also be protected and any data that is transferred across the network must be done so securely to protect the information from leak attacks. Encryption and decryption are best in this scenario.
- Conduct Employee Training: It is the best way to secure financial institutions and other organizations by not allowing any breach with strong and experienced manpower. People are always the biggest risk or strength in any organization’s security plan. Training should ensue on an ongoing basis, and it must be aimed at teaching employees the proper use of the systems without posing threats to security. Familiarizing them with the company’s security policies as a means of removing human components and limiting insider threats. An insider breach can cause a major loss than an outsider breach or fisher attack so the institutes must need to train their staff with the most advanced tactics.
- Maintain Rigorous Security Patching: Updating VDI hypervisors, virtual desktops, and corporate applications to address exploitable vulnerabilities at least weekly is recommended.
- Potential risks can be minimized through a formal RACI model approach to patch management.
- Adopt Multi-Factor Authentication: MFA is essential for securing remote corporate assets, to minimize dependence on passwords and threats that arise from compromised credentials. It is a security measure that requires users to provide more than just a password to log in to an account. MFA can help prevent unwanted access to accounts and systems by requiring users to provide two or more credentials.
It’s important to work with the financial team to ensure everyone agrees on using VDI for employees and applications. Both security and productivity need to be a top priority.
The following approaches can safeguard sensitive financial information while optimizing operational performance…
A. Policies on security should be well-elaborated
- Access Control
- Data Encryption
- Regular Security Audits
B. Maintain Regular Software Updates
Update VDI software, OS, and application software, or use the patch management tool to apply the latest security patches.
It is critical to capitalize on a patch management model that will help manage risks from a weak patch management system caused by outdated and vulnerable software.
C. Enhance Endpoint Security
Universal security is antivirus, firewalls, and IDS protocols as the endpoint protection solution.
Ensure security controls on the devices used to connect with the VDI setting.
D. Set Data Backup as well as Data Recovery Processes
Establish a strong data backup program which would entail backup of key financial data.
You should also customize a disaster recovery strategy that will act as a blueprint to get the systems back on track in a crash or a cyber-attack.
E. Conduct User Training Awareness Programs
- Strong Password Management
- Phishing Awareness
- Safe Usage Guidelines
Using a secure virtual desktop infrastructure can reduce threats and secure the data they manage while promoting efficient remote work. Such steps help to follow the regulations of the industry and reinforce the security from the new cyber threats.
Final Words
In a nutshell, it can be said that Virtual Desktop Infrastructure has become a revolutionary concept for financial institutions providing them with all the necessary features to become successful in the modern digital world. There are risks including data breaches, hypervisor risks and poor access control, however, all these are manageable risks. Realizations such as effective encryption/decryption formulas, frequent systems updating, and use of multi-factor authentication bring a big positive change to secure set-ups of virtual desktops. Moreover, it is essential to train the employees since most of the time, the problem is on the human end of the system.
With the help of the presented approach, risks are reviewed thoroughly, and the overall strategy allows financial organizations not only to protect/secure the information but also to guarantee smooth functioning and increased efficiency. Finally, it’s about protecting and optimizing while always being ready for something new, for the constant growth of threats and needs. If implemented correctly, VDI can be a foundation of secure and effective financial operations as intended.
Learn About VDI Virtual Desktop
FAQ
What are patch management tools?
A patch management tool, or patch management software, is an application designed to ensure computer systems and software stay updated with the most recent security updates and performance enhancements. Patch management tools can automate the process of keeping systems up to date, reduce the risk of vulnerabilities, ensure software and applications run smoothly and boost productivity.
What are the limitations of VDI?
High demands on the network bandwidth.
Possible problems of latency that might cause slow performance.
Difficulties in configuration, administration and protection for IT managers.
Is VDI safer than VPN?
Yes, VDI is safer than a VPN because:
A VPN does not mitigate risks arising from compromised end nodes.
VDI offers secure separated and controlled, virtual desktops in the cloud resulting in minimized risk.
How do you protect a VDI environment?
To secure a VDI environment, implement the following:
Remote procedures and the principle of working with minimal privileges.
The two most common best practices are vulnerability scanning and patch management.
Protect information by securing it during transmission and while stored using encryption techniques.
The monitoring of compliance for virtual desktops and hosting systems.
Why is it essential for financial organizations to optimize security systems and operational efficiency?
Business entities deal with valuable financial data and thus are vulnerable to cyber threats.
They can result in serious losses and reputational loss.
It is crucial to keep the business going to be able to meet the stiff competition and the ever-increasing needs of the financial market.
How financial institutes can mitigate security risks?
To mitigate these security risks, organizations can:
Keep virtual desktop images up to date by applying the most recent patches.
Implement automation to streamline the update process.
Leverage cutting-edge security tools, such as AI-powered systems, intrusion detection, and prevention technologies.
Implement industry-standard security practices
Conduct a VDI security assessment to receive recommendations for reducing security risks